Identity & Access Management You Can Trust
From strategy to execution, our IAM experts deliver scalable solutions that strengthen security, simplify access and enable digital transformation.
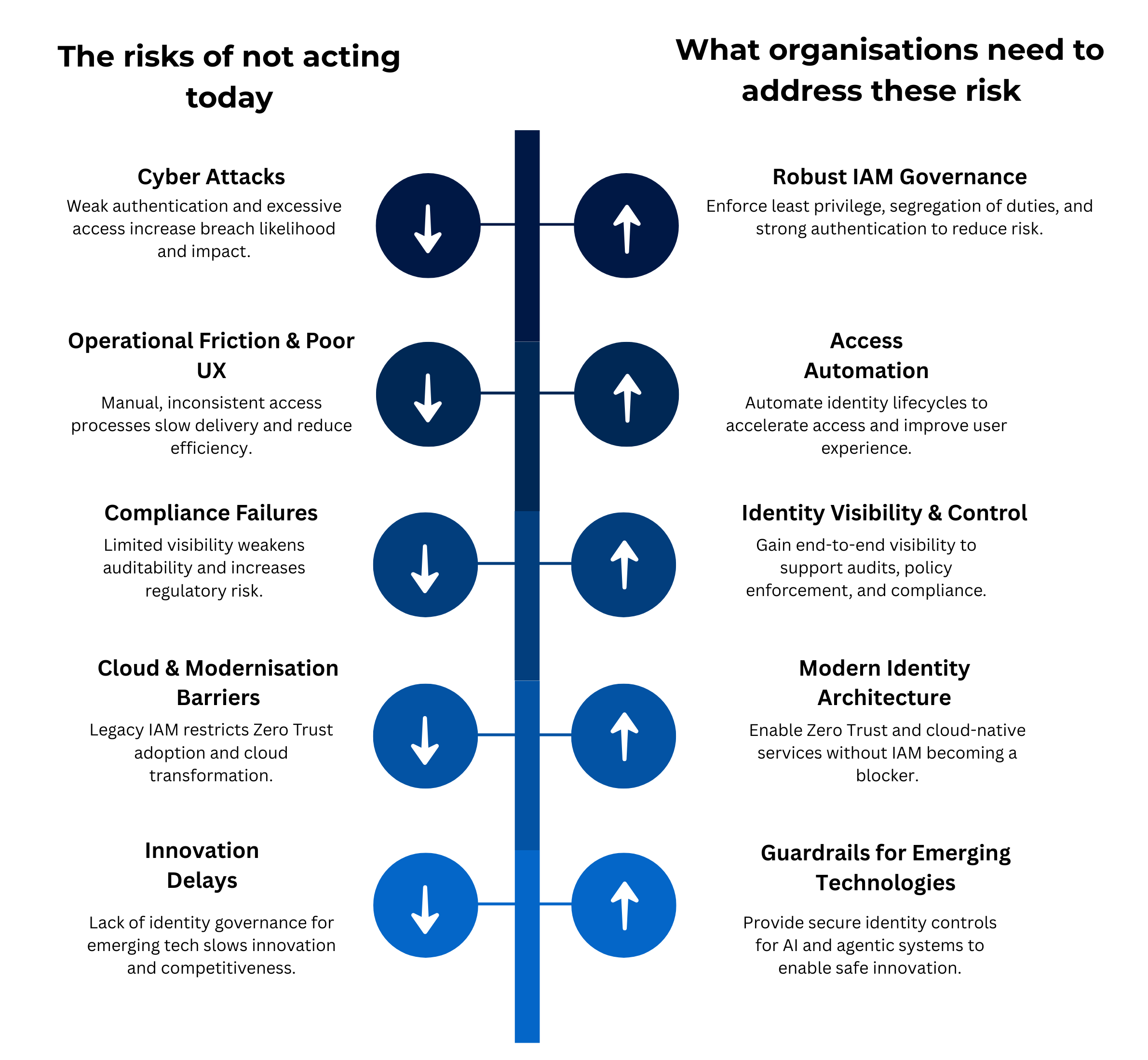
Identity is the new perimeter. It sits at the core of modern security - governing access across users, devices, applications, and emerging agentic identities. When IAM is weak or fragmented, risk propagates across the entire organisation.
Are You Confident the Right People Have the Right Access?
38%
of breaches are caused by stolen credentials - more than phishing or vulnerabilities combined.
Verizon Data Breach Investigations Report (DBIR), 2024
90%
of organisations experienced at least one identity-related security incident in 12 months.
Identity Defined Security Alliance (IDSA), 2023
23%
of organisations have mature IAM capabilities.
Ponemon Institute & GuidePoint Security, 2025
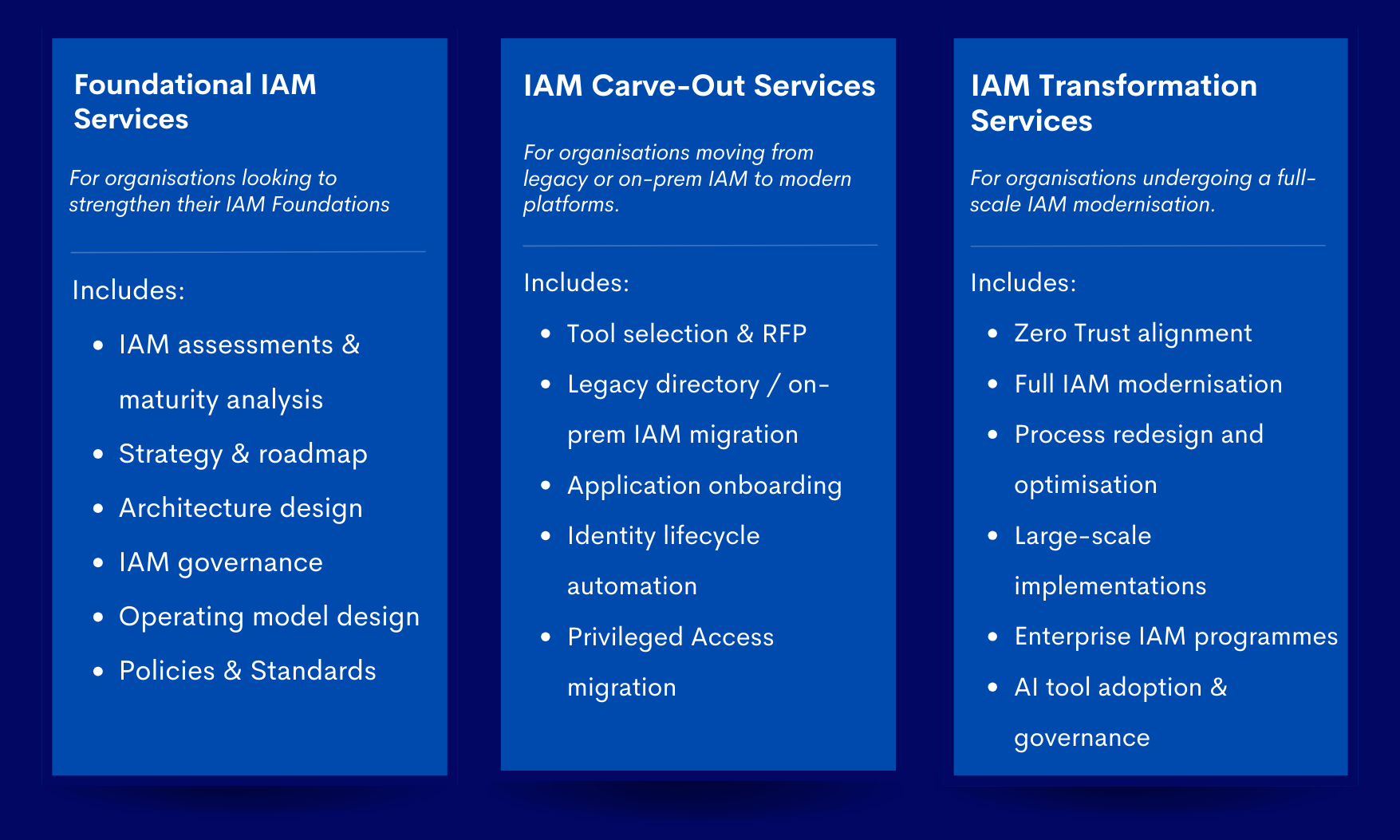
IAM Services that Secure and Scale
From Foundation to Transformation - We Build Identity That Lasts
What Makes Abicem the Correct IAM Partner of Choice
-
With over 20 years of enterprise IAM delivery experience, our team brings proven, hands-on expertise across Identity and Access Governance (IGA), Privileged Access Management (PAM), AI and agentic security, and large-scale transformation programs.
-
Our methodology starts with strategy, governance to ensure IAM initiatives are aligned to business priorities, regulatory requirements, and the target roadmap.
We establish the foundations for execution: IAM vision, target operating model, role and policy design, and governance frameworks.
-
IAM is inherently complex. We specialise in making it simple.
By removing unnecessary friction and rationalising identity flows, we embed with your teams to deliver IAM programs that are easy to operate, govern, and scale.
-
We design IAM around how users actually work - without compromising security or control. By prioritising clear, consistent access journeys, we deliver IAM solutions that reduce friction, improve adoption, and increase productivity across the organisation.
-
We don’t just design the target state - we embed within your teams to deliver it. Abicem leads IAM programs end-to-end, from strategy through execution, ensuring alignment, accountability, and measurable outcomes.
We then deliver at scale, executing seamless transformations across users, applications, and environments spanning Identity and Access Governance (IGA), Entra ID, Active Directory, SailPoint, PKI, and PAM.

Our Latest Project
Supporting the Novartis-Sandoz Separation
One Seamless Transition, Zero Disruption to Operations.
Abicem supported a global pharmaceutical spin-off to lead the analysis and migration of over 1,300 applications, 35,000 users and hundreds of OT Devices, including critical production sites.
Delivered under a strict TSA timeline, the programme ensured a seamless transition with no disruption to business operations.
Ready to take the next step?
Connect with our team to discuss your goals and explore how Abicem can help you achieve them.